We find that (cyber-)security awareness has arrived in German SMEs. Yet this awareness is not equally distributed between all staff, but mostly apparent in management and tech departments.
Despite improvements in defenses, this inequality might open up SMEs to more targeted attacks such as phishing, insider attacks, and advanced persistent threats.
Publication #
Nicolas Huaman, Bennet von Skarczinski, Christian Stransky, Dominik Wermke, Yasemin Acar, Arne Dreißigacker and Sascha Fahl.
30th USENIX Security Symposium (USENIX Security 2021), August 11-13, 2021.
Abstract
Cybercrime is on the rise. Hacker attacks, organized crime, and nation-state adversaries are an economic threat for companies world-wide. Small and medium-sized enterprises (SMEs) have increasingly become victims of cyberattacks in recent years. SMEs often lack the awareness and resources to deploy extensive information security measures.
However, the health of SMEs is critical for society: For example, in Germany, 38.8% of all employees work in SMEs, which contributed 31.9% of the German annual gross domestic product in 2018. Many guidelines and recommendations encourage companies to invest more into their information security measures. However, there is a lack of understanding of the adoption of security measures in SMEs, their risk perception with regards to cybercrime and their experiences with cyberattacks.
To address this gap in research, we performed 5,000 computer-assisted telephone-interviews (CATIs) with representatives of SMEs in Germany. We report on their experiences with cybercrime, management of information security and risk perception. We present and discuss empirical results of the adoption of both technical and organizational security measures and risk awareness in SMEs. We find that many technical security measures and basic awareness have been deployed in the majority of companies. We uncover differences in reporting cybercrime incidences for SMEs based on their industry sector, company size and security awareness. We conclude our work with a discussion of recommendations for future research, industry and policy makers.
Downloads
| Filename | Type | Copyright |
|---|---|---|
| conf-usenix-huaman21.pdf | Publication PDF | USENIX Open Access |
| cybercrime-replication.zip | Replication Package for our Study | CC-BY-SA |
Overview #
Cybercrime conducted by hackers, organized crime, and nation-state adversaries is an economic threat for companies world-wide. Small and medium-sized enterprises (SMEs) have increasingly become victims of cyberattacks in recent years.
Opposed to large scale companies, SMEs often lack the awareness and resources to deploy extensive information security measures and to maintain them.
We set out investigate this effect on cybercrime incidents and countermeasures by interviewing 5000 SMEs in Germany, Our goal was to interview employees responsible for information technology or security and ask them about their experiences and problems with cybercrime, as well as their perception of risks and handling of information security.
Our methodology was as follows:
- Design Phase: Literature review, 6 expert interviews, input from regional business advisory council.
- Sampling: Stratified random sampling (n=5000) by industry sector.
- Piloting: Testing with 12 security experts, 5 telephone interviews, iterating interview guide.
- Training: Training 141 telephone interviewers.
- Interviews: 5000 computer assisted telephone interviews (CATI).
- Analysis: Quality check & anonymization, open coding & evaluation.
Interviews #
We developed the final interview questions based on a literature review, the help of six expert interviews, and multiple feedback rounds with information security and privacy experts from industry and academia.
Data was collected in the form of computer-assisted telephone interviews (CATI) with the help of a professional survey institute employing experienced, trained interviewers. In preparation of the interviews, we performed interview training sessions with the 141 interviewers in two on-site call centers of the CATI service provider.
The CAT-Interview guide had the following structure:
CATI Questionnaire
(This is a translation of the German interview guide)
- The questions are in the form of “
Question? (Choices → Factor in Regression [B:Baseline]), (Scale)”. - The response options “not specified” and “I do not know” were present for all questions, but are omitted here.
- WZ08-Classification of the
Industries → Industry Sector [B:Construction]andheadcount bins → Headcountwere adopted from the underlying commercial sampling databases.
A.1 “Company” - Introduction
- “In which area do you work in your company?"
[multiple answers possible] → Interviewee Position(Multiple Choice: Executive/Management Board, IT & Information Security, Data Protection, Plant Security, Audit, External Service Provider, Other [free text]) - “How high do you estimate the risk for your company to be harmed by a cyber-attack in the next 12 months …"
(Scale: Very low, Rather low, Rather high, Very high)
- ”… that also hits many other companies at the same time?"
(e.g. mass sent malware);
→ Risk Assessment Untargeted - ”… that exclusively affects your company?"
(e.g. targeted espionage attack);
→ Risk Assessment Targeted
- ”… that also hits many other companies at the same time?"
(e.g. mass sent malware);
A.2 “Incidence” - Detected cyber-attacks
Always related to the last 12 months:
- “How often has your organization been affected by and had to actively respond to the following types of attacks?"
(Scale: Amount […])
- Ransomware - which was intended to encrypt company data;
→ Ransomware - Spyware - which was intended to spy on user activities or other data, Other malicious software e.g. viruses/worms/trojans;
→ Spyware & Other Malicious Software - Manual hacking - i.e. misconfiguration and manipulation of hardware and software without the use of special malware;
→ Manual Hacking - Denial of Service ((D)DoS) - attacks aimed at overloading web or e-mail servers, defacing attacks aimed at unauthorised alteration of company web content;
→ (D)DOS - CEO fraud - in which a company leader was faked in order to effect certain actions by employees;
→ CEO-Fraud - Phishing - in which employees were deceived with genuine-looking e-mails or websites, e.g., in order to obtain sensitive company data;
→ Phishing
- Ransomware - which was intended to encrypt company data;
A.3 “Measures” - Information security measures
- “Which of the following measures are currently in place in your company?"
(Scale: Yes, no)
- Written information security guidelines, written guidelines for emergency management;
→ Information Security Policy/Incident Response Plan - Compliance with the guidelines is checked regularly and violations are punished if necessary;
→ Information Security Policy Enforcement - Regular risk and vulnerability analyses (incl. pen-test);
→ Risk Analysis - Certification of information security (e.g. in accordance with ISO 27001 or VdS 3473);
→ Information Security Certification - Information security training for employees;
→ Information Security - Training, Exercises or simulations for the failure of important IT systems;
→ Emergency Drills - Minimum requirements for passwords;
→ Password Requirements - Individual assignment of access and user rights depending on the task;
→ Individual Access Control - Regular data backups, Physically separate storage of backups;
→ Regular Data Backups/Separate Backup Location - Up-to-date antivirus software;
→ Antivirus Software - Regular and prompt installation of available security updates and patches; `→ Regular Security Updates``
- Protection of IT systems with a firewall;
→ Firewall
- Written information security guidelines, written guidelines for emergency management;
- “What is your impression? Would you say …"
- ” … The management is aware of the IT risks consciously and adheres to the specifications”;
→ Information Security Sensitivity Management - ” … The staff is aware of the IT risks consciously and adheres to the specifications";
→ Information Security Sensitivity Employees - " … In the company a lot is done for information security" [INT.: more than classical protective measures];
→ Information Security Investment
- ” … The management is aware of the IT risks consciously and adheres to the specifications”;
A.4 “Demographics” - Company characteristics
- “When was your company founded?"
(year [free text], ≤ 2 years, < 10 years, < 25 years, < 100 years, ≥ 100
years);
→ Company Age [B:< 10 years] - “How high was the total turnover of your company in the last financial year?"
(Total sales [free text], ≤ 500,000 C, < 1 million C, < 2 million C, < 10 million C, < 50 million C, < 500 million C, ≥ 500 million C);
→ Annual Turnover - “Does your company export products or services?"
(Yes, no);
→ Export Activity - “How many locations with their own IT infrastructure does your company have …"
- ” … Locations in Germany”;
→ Multiple National Locations - ” … Locations abroad”;
→ International Locations
- ” … Locations in Germany”;
- “How many employees of your company invest the majority of their working time in … “
(Scale: Number [free text]);
- ”… the operation of IT in general?";
→ Employees Tech
- ”… the operation of IT in general?";
- “Has your company outsourced IT functions” (Multiple answers possible)
→ Outsourced IT Security- Email & Communication
- Network Administration & Maintenance
- Web Presence (e.g. Online Marketplaces, Shops, Customer Portals)
- Cloud Software & Cloud Storage
- Information Security (e.g. Incident Detection, SIEM, Threat Intelligence)
- Other [Free text]
- No IT Functions outsourced
The interviews were conducted from a stratified random sample of 5,000 organizations. Stratified sampling is a method to sample from a population by partitioning the population into subpopulations.
The population of companies in Germany is partitioned based on industry sectors and company sizes:
- Industry Sectors. In order to ease international comparability and connectivity to other official studies, we use the official German Industry Classification WZ08 system. WZ08 is based on the European NACE Revision 2 classification, which in turn is based on ISIC Rev 4 classification of the United Nations.
- Company Size. We created the subgroups for company size based on the Commission Recommendation (2003/361/EC). This definition is standard across statistics related to European and German SMEs, which allows for comparisons between our results and those of similar studies.
The CATI service provider drew the sample from two commercial company databases. The databases, according to their self-declaration, combined contain all small, medium-sized, and large companies in Germany.
We aimed to interview employees responsible for information security. In cases were information security was outsourced to external service providers or taken over by employees of other areas, we invited a representative of the board or in other related roles.
Findings #
In this section we report and discuss results of all 5,000 CAT-interviews. We report and discuss company demographics, risk perceptions of employees, deployed security measures, and detected attacks.
Companies
We interviewed employees in charge of their company’s information technology (IT) or security (69.7%; 3,484), as well as employees in management board positions (23.4%; 1,171). Additionally, we interviewed representatives responsible for company audits (2.1%; 104), data protection (6.8%; 342) and factory safety (1.1%; 56), as well as representatives that did not fit in one of the above categories (8.0%; 402).
With increasing company size, our interview partner was more likely to be dedicated information technology staff. In smaller companies, we mostly relied on interviews with executive management.
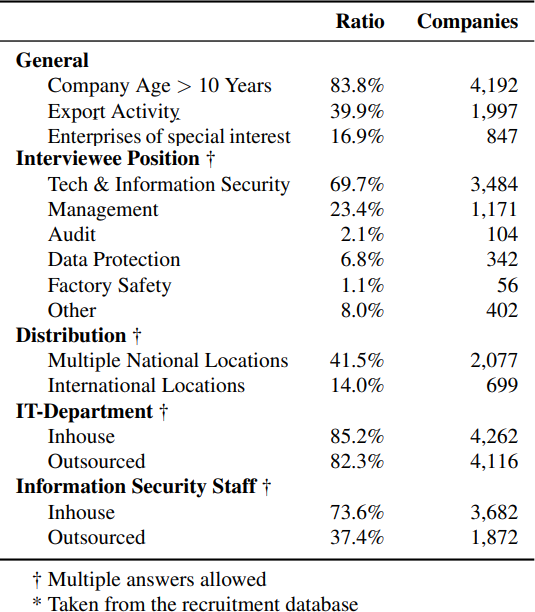
Figure 1: Demographics for our stratified sample of 5000 companies. For the stratified sample, the CATI service provider obtained 1,000 companies of each subgroup and companies in each company size subgroup for SMEs, as well as 500 companies with 500 or more employees. Large organizations and organizations providing services of general interest are thus more strongly represented in the sample.
- IT Staff: About 85.2% (4,262) of the participants stated that their company employes dedicated information technology (IT) staff, and 82.3% of companies had purchased IT services from external providers. Hence, 3,511 (70.2%) run both their own IT department and purchase external IT services.
- Information Security Staff: The majority (73.6%; 3,682) of companies has dedicated information security staff, while 37.4% (1,872) rely on external information security service providers. 24.4%(1,220) exclusively rely on external information security services.
Information Security Sensitivity
To assess information security sensitivity, we asked interviewees in three question categories. We focused on the awareness of information security risks:
- Of the management board.
- Regular employees and their compliance with information security policies.
- And if the company actively advances information security (e.g., by investing in new information security technologies).
Key Findings: Information Security Sensitivity.
- Company Position: While management made up a smaller portion of the interviewee sample, they reported higher sensitivity scores than regular employees. Staff in tech positions tended to report lower scores across all areas.
- Company Type: Finance and communication industries received higher sensitivity scores in general
Risk Perception
We asked interviewees to estimate the risk of their company to fall victim of cyberattacks within the next 12 months. We distinguished between:
- Targeted attacks (i.e., attacks that would only threaten their company specifically).
- And mass attacks (i.e., attacks that would threaten other companies as well).
In general, interviewees reported significantly lower risks for a targeted attack (8.7%) than for a mass attack (34.9%).
Key Findings: Risk Perception.
- Company Size: Interviewees working for small companies reported a lower perceived risk of being attacked than interviewees working for larger companies.
- Targeted vs. General Attacks: Most interviewees assess the risk for their company being hit by a targeted attack lower as the risk of being hit by a mass attack.
Security Measures
We asked interviewees to report deployed security measures in their companies and distinguished between:
- Technical measures (e.g., firewall)
- Organizational measures (e.g., incident response plans)
The heatmap below illustrates the deployment likelihood of both technical and organizational security measures within different company size:
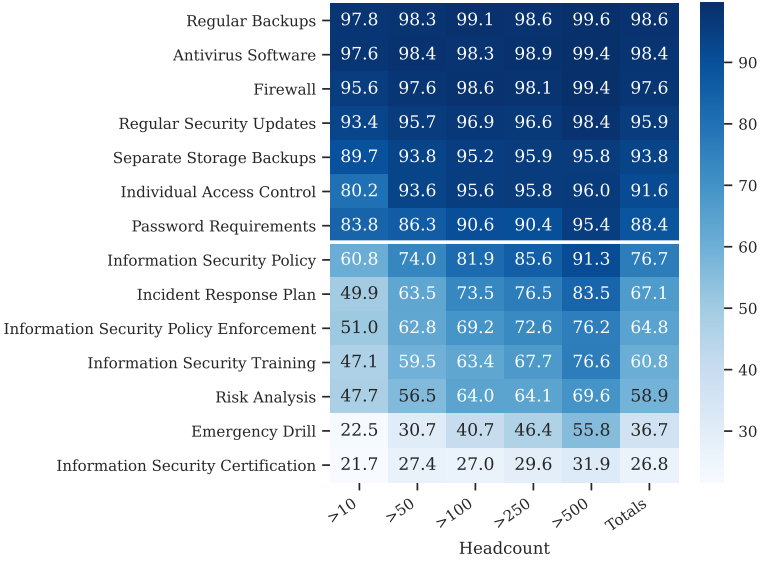
Figure 2: Heatmap of technical (top half) and organizational (bottom half) security measures reported by our interviewees.
Technical security measures. The majority of the interviewees reported that their companies deploy technical security measures.
- More than 90% reported that they use firewalls, regularly patch and update their systems, use up-to-date anti-virus software, deploy effective access control mechanisms, and secure backup strategies.
While we cannot provide an in-depth analysis of respective technologies and deployment quality or maturity, our results indicate that many common technical security measures find widespread adoption in companies.
Key Findings: Technical Security Measures
- We find that basic technical security measures are widely deployed, even in small companies.
- Different industry sectors, company headcounts, company ages, and the use of external information security expertise all show significant differences in the adoption of technical security measures.
Organizational security measures. In contrast, the adoption of organizational measures is lower in general and more diverse.
- Most interviewees reported written security and privacy policies (78.7%) and that they get regularly reviewed and revised if necessary (79.4%). Only 29.9% report security certifications or exercises or simulated the failures of computer systems in their companies (37.4%).
Again, we cannot provide more in-depth details of the quality or maturity of policies or the type of security certification.
Key Findings: Organizatorial Security Measures.
- Organizational measures have lower adoption rates in SMEs than technical measures.
- We find that company size correlates with all organizational security measures in our analysis.
- Companies in the Finance & Insurance and Energy & Gas sectors are more likely to deploy organizational security measures.
Reported Incidents
We asked participants to report the security incidents their company detected and reacted to in the last 12 months.We explicitly asked participants to not report incidents that could be dealt with automatically, e.g., spam e-mails that were automatically blocked using anti-virus software or spam filters.
- 45.1% of the participants reported that their company had to actively react to at least one incident in the last 12 months. With more than half of them (1,842) being attacked more than once.
We specifically asked interviewees to report on CEO-Fraud, DDoS, defacing, manual hacking, phishing, ransomware, and spyware & other malware.
- We find that multiple national company locations correlat with the reporting of incidents including ransomware, spyware & other malware, manual hacking/advanced persistent threat, DDoS, CEO-fraud, and phishing.
- Participants who reported active enforcement of information security policies or incident response plans were less likely to report attacks in all incident categories except for DDoS.
- Reporting export activity was positively correlated with reporting spyware and other malware.
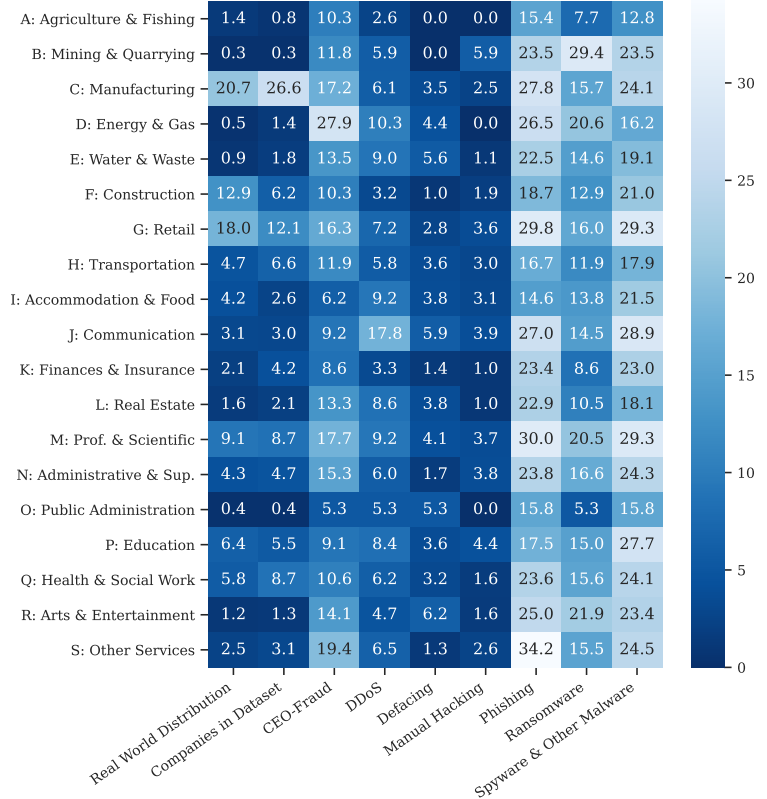
Figure 3: Heatmap of percentage of companies per sector that have experienced a certain type of attack.
Key Findings: Reported Incidents.
- Organizational measures more frequently map to the reporting of security incidents than reported technical security measurements.
- Larger companies, especially with dedicated tech departments, reported more incidents.
Considerations #
- Focus on SMEs in Germany: Our results may not be generalizable to SMEs in other countries. It may also be likely, that micro-enterprises and very large enterprises differ in results. However, small and medium-sized businesses make up 38.8% of all employees and 17.6% of enterprises in Germany, generating 31.9% of the gross domestic product.
- Population: We used two commercial company databases. According to their self-declaration, the databases should include all registered companies in Germany. If this is not the case, certain organizations from the population might not have had the chance to be included in the sample.
- Desirablility Bias: The sensitive questions we asked in our security survey might have introduced a desirability bias. Interviewees might have had concerns to answer questions truthfully or participate at all. To combat this bias, we asked for facts about existing and past company policy and history instead of asking for desires and plans. Furthermore, our recruitment email, briefing and consent form clarified that results will be handled anonymously and only reported in aggregated form, and that we are not rating company security, but investigating the prevalence of cybercrime across companies.
- Selection Bias: We found that companies with fewer than 50 employees more often declined participation in the CAT-Interview. Similarly, companies in certain industries tend to deviate from average participation rates by at most 6%, which we deemed negligible for our results.
- Self-reporting Bias: Like all surveys and interviews, we have to expect a self-reporting bias. Since we interviewed only one representative for each company, the data we collected is subjective and informed by individual knowledge, motivation, and attitudes. While we preferred tech staff responsible for information security (e.g., chief information officers, security engineers, or DevOps) as interviewees, not all companies had such staff available.
- CATI Restrictions: Due to time and complexity restrictions of CAT-Interviews our study is limited in insights regarding the maturity level and implementation details of security measures and attacks. For example, two participants confirmed the existence of password policies in their companies without being able to provide detailed information about the policies.
Summary #
We surveyed 5000 small and medium enterprises (SMEs) in Germany using computer assisted telephone interviews (CATI) to determine cybercrime threats they face and countermeasures they deploy. We aimed to interview employees responsible for information technology or security and asked them about their experiences and problems with cybercrime, as well as their perception of risks and handling of information security.
In relation to our research questions in the paper, we summarize the following key findings:
How do company employees perceive the risk of cyberattacks?
- In general, our interviewees did not perceive a high risk of cyberattacks for their companies.
- They perceived the risk of mass attacks higher than the risk of targeted attacks — especially interviewees working for smaller companies.
- This lower perceived risk of targeted attacks might make them more susceptible to attacks such CEO-Fraud, or targeted ransomware attacks as well as insider threats.
Which and how frequent are information security measures deployed in SMEs?
- Most of our interviewees reported the deployment of technical measures such as firewalls and antivirus software compared to less frequently reported organizational measures such as certifications for information security.
- We found a high variance within reported organizational measures, with measures that require regular active engagement such as information security training, risk analysis, or emergency drills being less frequently reported.
- Together with the low perceived risk of targeted cyberattacks, this might make companies particularly vulnerable to targeted attacks like CEO-Fraud and insider-threats.
“Which types and frequencies of attacks have our participating companies detected within the last 12 months?
- Most companies reported incidents such as phishing and malware. CEO-Fraud and (D)DoS attacks also appeared to be common problems. Defacing and manual hacking were rarely reported.
“How are deployed security measures and company characteristics related to reported incidents and what are the emerging victimization factors?"
- Certain company demographics such as international activity and company size contributed to more frequent reports of incidents by interviewees.
- This also relates to the more frequent reporting of incidents by interviewees working for companies with multiple locations (likey due to a larger attack surface).
- We found that interviewees working in particular industry sectors reported certain incidents more frequently:
- CEO-Fraud (Energy and Gas)
- (D)DoS (Communication)
- Defacing (Mining)
Recommendations
Based on our findings, we can give a number of recommendations:
For Companies
- Role of Management. An interesting tendency in our analysis is, that the risk sensitivity of the management generally was rated higher than the sensitivity of company staff.
- Management should aim to spread this self-reported awareness to company staff.
- Management could provide opportunities to raise information security awareness (e.g., by security training), especially for staff not directly involved in tech.
For Governments/Legislators
- Guidelines & Requirements: We find that industry sectors with higher security requirements by law (Finances & Insurance and Energy & Gas) reported fewer incidents despite strong detection mechanisms. This might suggest a positive effect of external guidelines and requirements on security.
- Risk Awareness: Our descriptive results show that risk awareness and assessment is still low. Legislators could actively work on increasing awareness for information security and the risks of cybercrime.
For Governments/Legislators
- Tech Staff vs. Management: We find a strong discrepancy between tech and management in both risk assessment and deployed measures. This disparity could be an interesting venue for future work.
- Industry Sector: We noticed outliers in the correlation of industry sectors and incidents. An in-depth investigation could reveal how to improve security for these specific sectors.
- Maturity of Measures: Technical measures had very high reporting rates, but we suspect that the security impact of measures like access control and firewall setup can vary widely based on the implementation quality and maturity.
Replication Package #
To enhance replicability of our study, we provide a replication package with our interview documents. We translated the original documents from German to English. Due to the sensitive nature of collected data, we assured our participants that no raw data will be published.
Replication Package/
ENG_Constent form CATI Survey.docx: Consent form for the computer assisted telephone interview.ENG_Briefing for interviewers.docx: Briefing document for the CAT interviewers.ENG_BMWI Motivation Letter.docx: Follow-up recruitment letter.ENG_Recruitment Email.docx: Initial recruitment letter.ENG_Expert interview guide.docx: Guide used for the initial expert inteviews during piloting.ENG_Survey - Relevant Questions (Translated).docx: Translated from German.ENG_Info tab expert interviews.docx: Demographics table of experts interviewed during piloting.
We hope this replication package helps future studies to better compare and position themselves to our work.
Cite This Work #
Feel free to cite this publication as:
@inproceedings{huaman2021large,
author = {Nicolas Huaman and Bennet von Skarczinski and Christian Stransky and Dominik Wermke and Yasemin Acar and Arne Drei{\ss}igacker and Sascha Fahl},
title = {A Large-Scale Interview Study on Information Security in and Attacks against Small and Medium-sized Enterprises},
booktitle = {30th {USENIX} Security Symposium ({USENIX} Security 21)},
isbn = {978-1-939133-24-3},
pages = {1235--1252},
url = {https://www.usenix.org/conference/usenixsecurity21/presentation/huaman},
publisher = {{USENIX} Association},
month = aug,
year = {2021},
}Huaman, Nicolas, et al. "A Large-Scale Interview Study on Information Security in and Attacks against Small and Medium-sized Enterprises." 30th {USENIX} Security Symposium ({USENIX} Security 21). 2021.Huaman, N., von Skarczinski, B., Stransky, C., Wermke, D., Acar, Y., Dreißigacker, A., & Fahl, S. (2021). A Large-Scale Interview Study on Information Security in and Attacks against Small and Medium-sized Enterprises. In 30th {USENIX} Security Symposium ({USENIX} Security 21).%0 Journal Article
%T They Would do Better if They Worked Together: The Case of Interaction Problems Between Password Managers and Websites
%A HuamanC, Nicolas
%A Amft, Sabrina
%A OltroggeC, Marten
%A Acar, Yasemin
%A FahlC, SaschaTY - CONF
T1 - A Large-Scale Interview Study on Information Security in and Attacks against Small and Medium-sized Enterprises
A1 - Huaman, Nicolas
A1 - von Skarczinski, Bennet
A1 - Stransky, Christian
A1 - Wermke, Dominik
A1 - Acar, Yasemin
A1 - Dreißigacker, Arne
A1 - Fahl, Sascha
JO - 30th {USENIX} Security Symposium ({USENIX} Security 21)
Y1 - 2021
ER - 
